Evilginx2 Advanced Phishing Attack Framework
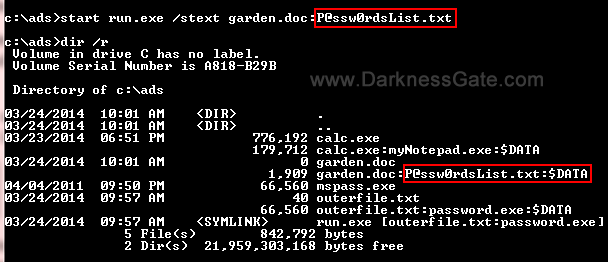
This is the successor of Evilginx 1, and it stays in-line with the MITM lineage. This tool is designed for a Phishing attack to capture login credentials and a session cookie. Table of Content Overview Setup Perquisites Installation Domain Setup Priming Evilginx Execution Lure Creation Attack Simulation Overview One of the biggest concerns in…