Hacking – Skills
As an ethical hacker, you will need to understand various hacking techniques such as −
- Password guessing and cracking
- Session hijacking
- Session spoofing
- Network traffic sniffing
- Denial of Service attacks
- Exploiting buffer overflow vulnerabilities
- SQL injection
In this chapter, we will discuss some of the skills that you would require to become an expert in Ethical Hacking.
Basic Skills
Computer hacking is a science as well as an art. Like any other expertise, you need to put a lot of effort to gain knowledge and become an expert hacker. Once you’re on track, you’ll need more effort to keep up-to-date with the latest technologies, new vulnerabilities, and exploitation techniques.
Ethical hackers must specialize in computer systems and have very strong programming and computer networking skills.
A moral hacker requires a lot of patience, perseverance and perseverance to try again and wait for the required result.
Additionally, an ethical hacker needs to be smart enough to understand the situation and the minds of other users to implement the feats of social engineering. A good ethical hacker also possesses great problem solving skills.
Courses & Certifications
This tutorial provides basic guidelines for becoming a successful ethical hacker. If you want to excel in this field, you can choose to pursue the following courses and certifications
- Obtain a bachelor’s degree in Computer Science or A+ Certificate to gain an understanding of the most common hardware and software technologies.
- Get into a programmer’s role for a few years and then switch to get a tech support position.
- Proceed to get network certifications like Network+ or CCNA and then security certifications like Security+, CISSP, or TICSA.
- It is recommended that you get some work experience as a Network Engineer and System Administrator to understand networks and systems inside out.
- Keep going through various books, tutorials and papers to understand various computer security aspects and take them as a challenge to secure your network and computer systems as network security engineer.
- Study courses which cover creating Trojan horses, backdoors, viruses, and worms, denial of service (DoS) attacks, SQL injection, buffer overflow, session hijacking, and system hacking.
- Master the art of penetration testing, footprinting and reconnaissance, and social engineering.
- Finally go for a Certified Ethical Hacker (CEH) Certification.
GIAC (Global Information Assurance Certification) and Offensive Security Certified Professional (OSCP) are additional IT security certifications which will add a lot of value to your profile.
Final Note
You need to stay as a White Hat Hacker which means you need to work within given boundaries. Never intrude or attack any computer or network without a required permission from the authorities.
As a final note, it is highly recommended that you refrain from engaging yourself in black hat hacking which may spoil your entire career.
Ethical Hacking – Process
Like all good projects, ethical hacking also has a set of distinct steps. It helps hackers to have a structured ethical hacking attack.
Different security training manuals explain the process of ethical hacking in various ways, but for me as a certified ethical hacker, the entire process can be classified into the following six steps.
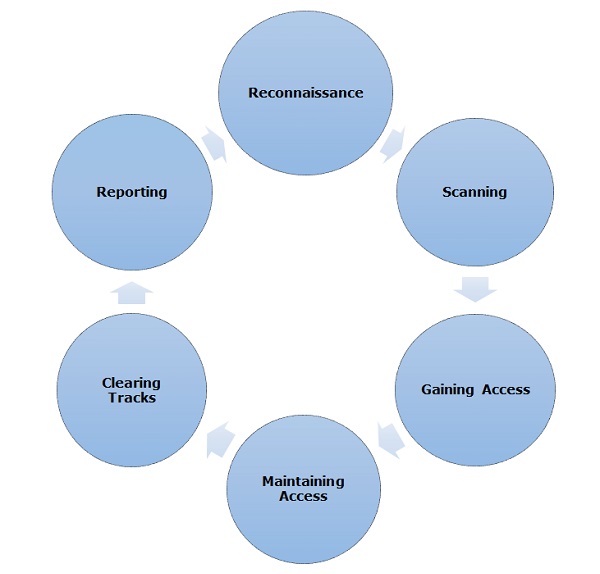
Reconnaissance
Reconnaissance is the stage where the attacker gathers information about the target using active or passive means. Tools widely used in this process are NMAP, Happening, Maltego and Google Dork.
Scanning
In this process, the attacker begins to actively examine the target machine or network for vulnerabilities that can be exploited. The devices used in this process are Nessus, Nexpose, and NMAP.
Gaining Access
In this process, the vulnerability is located and you attempt to exploit it in order to enter into the system. The primary tool that is used in this process is Metasploit.
Maintaining Access
This is the process where the hacker has already gained access to a system. After gaining access, the hacker installs some backdoor to enter the system when it needs access to this proprietary system in the future. Metasploit is the preferred tool in this process.
Clearing Tracks
This process is actually an immoral activity. This has to do with deleting the logs of all activities occurring during the hacking process.
Reporting
Reporting is the final step to eliminate the ethical hacking process. Here Ethical Hacker compiles a report with its findings and work such as the tools used, success rate, vulnerabilities detection and exploitation process.
Quick Tip
Procedures are not standard. You can adopt a set of different processes and tools according to your techniques with which you are comfortable. The process has the least importance as long as you are able to achieve the desired result.
Ethical Hacking – Reconnaissance
Information gathering and knowing target systems are the first processes in ethical hacking. Reconnaissance is a group of procedures and techniques (footprinting, scanning, and computation) that are used to secretly find and collect information about a target system.
During reconnaissance, a moral hacker attempts to gather as much information as possible about a targeted system, which follows the seven steps listed below –
- Gather initial information
- Determine the network range
- Identify active machines
- Discover open ports and access points
- Fingerprint the operating system
- Uncover services on ports
- Map the network
We will discuss all these steps in detail in later chapters of this tutorial. Reconnaissance occurs in two parts – active reconnaissance and passive reconnaissance.
Active Reconnaissance
In this process, you will contact the computer system directly to obtain information. This information can be relevant and accurate. But if you are planning active reconnaissance without permission, then there is a risk of detection. If you are detected, the system administrator can take serious action against you and stop your subsequent activities.
Passive Reconnaissance
In this process, you will not connect directly to the computer system. This process is used to collect the necessary information without interacting with the target systems.










good article
A man is known by the company he keeps.
Hi, I do think this is an excellent blog. I stumbledupon it 😉 I may come
back once again since I book marked it. Money and freedom is the best way to
change, may you be rich and continue to guide other people.
Faint heart never won fair lady.
The mob has many heads but no brains.
I know this if off topic but I’m looking into starting my own blog and was curious what all is
needed to get set up?
I’m assuming having a blog like yours would cost a
pretty penny?
I’m not very web savvy so I’m not 100% positive.
Any recommendations or advice would be greatly appreciated.
Thank you