Scanning Webservers with Nikto for vulnerabilities
Nikto is a very popular and easy to use webserver assessment tool to find potential problems and vulnerabilities very quickly. This tutorial shows you how to scan webservers for vulnerabilities using Nikto in Kali Linux. Nikto comes standard as a tool with Kali Linux and should be your first choice when pen testing webservers and web applications.
Nikto is scanning for 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers according to the official Nikto website.
You should know that Nikto is not designed as a stealthy tool and scans the target in the fastest way possible which makes the scanning process very obvious in the log files of an intrusion detection systems (IDS) | Scanning Webservers
Scanning web servers for vulnerabilities is an important step in securing a network and identifying potential threats. One tool that can be used for this purpose is Nikto, a web server scanner that is designed to identify known vulnerabilities in web servers and web applications | Scanning Webservers
Nikto is a command-line tool that can be used to scan web servers for a wide range of known vulnerabilities, including those in the operating system, web server software, and web applications. It uses a database of known vulnerabilities and checks for specific versions of software and configurations that are known to be vulnerable. | Scanning Webservers
To use Nikto, an individual or organization would need to provide the IP or hostname of the web server they wish to scan, and any optional flags that they would like to use, such as specific ports or protocols to scan. The tool will then conduct the scan and output any identified vulnerabilities. | Scanning Webservers
The tool is able to scan for vulnerabilities in various web servers such as Apache, IIS, and others. It can also scan for specific web applications such as WordPress, Joomla, and more. The tool can also check for various misconfigurations, such as those in the HTTP headers, that can open a web server to attack. | Scanning Webservers
Nikto can also be used to check for the presence of specific files or scripts that may indicate a vulnerability. For example, it can check for the presence of specific PHP scripts that are known to be vulnerable, or for the presence of files that may indicate the presence of a vulnerable web application.
It’s important to note that Nikto is not a replacement for a comprehensive vulnerability management program. A comprehensive security program should include multiple tools and techniques
Nikto comes with the following features:
Features
These are some of the major features in the current version:
- SSL Support (Unix with OpenSSL or maybe Windows with ActiveState’s
Perl/NetSSL) - Full HTTP proxy support
- Checks for outdated server components
- Save reports in plain text, XML, HTML, NBE or CSV
- Template engine to easily customize reports
- Scan multiple ports on a server, or multiple servers via input file (including nmap output)
- LibWhisker’s IDS encoding techniques
- Easily updated via command line
- Identifies installed software via headers, favicons and files
- Host authentication with Basic and NTLM
- Subdomain guessing
- Apache and cgiwrap username enumeration
- Mutation techniques to “fish” for content on web servers
- Scan tuning to include or exclude entire classes of vulnerability
checks - Guess credentials for authorization realms (including many default id/pw combos)
- Authorization guessing handles any directory, not just the root
directory - Enhanced false positive reduction via multiple methods: headers,
page content, and content hashing - Reports “unusual” headers seen
- Interactive status, pause and changes to verbosity settings
- Save full request/response for positive tests
- Replay saved positive requests
- Maximum execution time per target
- Auto-pause at a specified time
- Checks for common “parking” sites
- Logging to Metasploit
- Thorough documentation
Another nice feature in Nikto is the possibility to define the test using the -Tuning parameter. This will let you run only the tests you need which can save you a lot of time:
0 – File Upload
1 – Interesting File / Seen in logs
2 – Misconfiguration / Default File
3 – Information Disclosure
4 – Injection (XSS/Script/HTML)
5 – Remote File Retrieval – Inside Web Root
6 – Denial of Service
7 – Remote File Retrieval – Server Wide
8 – Command Execution / Remote Shell
9 – SQL Injection
a – Authentication Bypass
b – Software Identification
c – Remote Source Inclusion
x – Reverse Tuning Options (i.e., include all except specified)
Nikto has it’s own updating mechanism. We encourage you to check for updates before using Nikto. Nikto can be updated using the following command:
nikto -update
Scanning webservers with Nikto
Let’s start Nikto to scan for interesting files with option 1 using the following command:
nikto -host [hostname or IP]-Tuning 1
Please not that may be illegal and punishable by law to scan hosts without written permission. Do not use nikto on HackingTutorials.org but use Virtual machines for practice and test purposes.
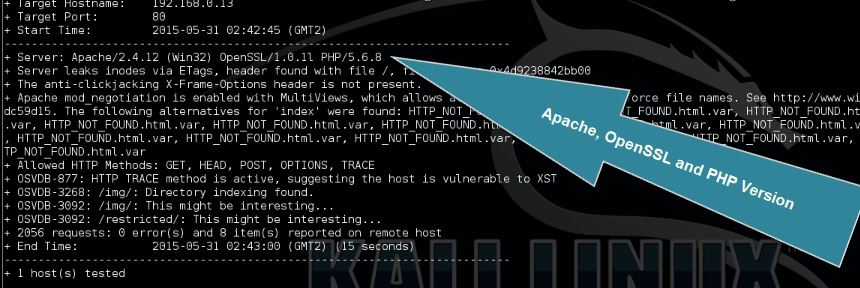
Nikto will now display the Apache, OpenSSL and PHP version of the targeted webserver. Also it will give you an overview of possible vulnerabilities including the Open Source Vulnerabilities Database (OSVDB) reference. When you search the OSVDB website for the reference code
it will explain the possible vulnerability in more detail. The OSVDB project currently covers more than 120,980 vulnerabilities, spanning 198,973 products from 4,735 researchers, over 113 years.
Running all Nikto scans against a host
To run all scans against a particular host you can use the following command:
nikto -host [hostname or IP]
Running all scans will take a lot of time to complete.
Running Nikto against multiple hosts
Nikto offers several options to test multiple hosts:
- By using a valid hosts file containing one host per line
- Piping Nmap output to Nikto.
A valid host file is a text file containing the hosts, you have to use one line for each host in order to make it valid for Nikto. Instead of using the hostname as an argument for the -h option you should use the filepath to the valid hosts file.
Another solution is to pipe the Nmap output to Nikto. Nmap will output the valid hosts to Nikto and Nikto will run the selected scans against these hosts.
The following command will run a Nmap scan on host 192.168.0.0 – 192.168.0.24 using a grepable output which is defined by the -oG- flag:
nmap -p80 192.168.0.0/24 -oG – | nikto -h –
Please note that you should use a dash (-) for Nikto’s host option to use the hosts supplied by Nmap.