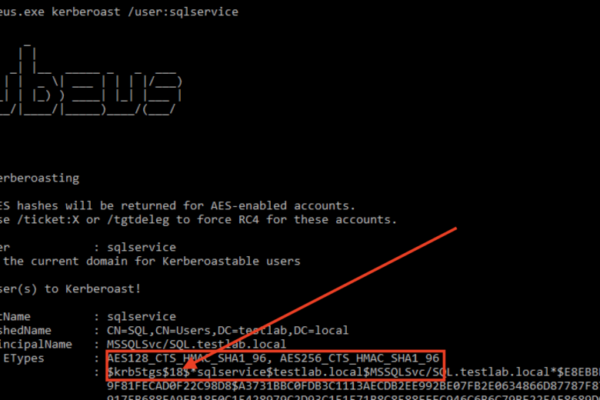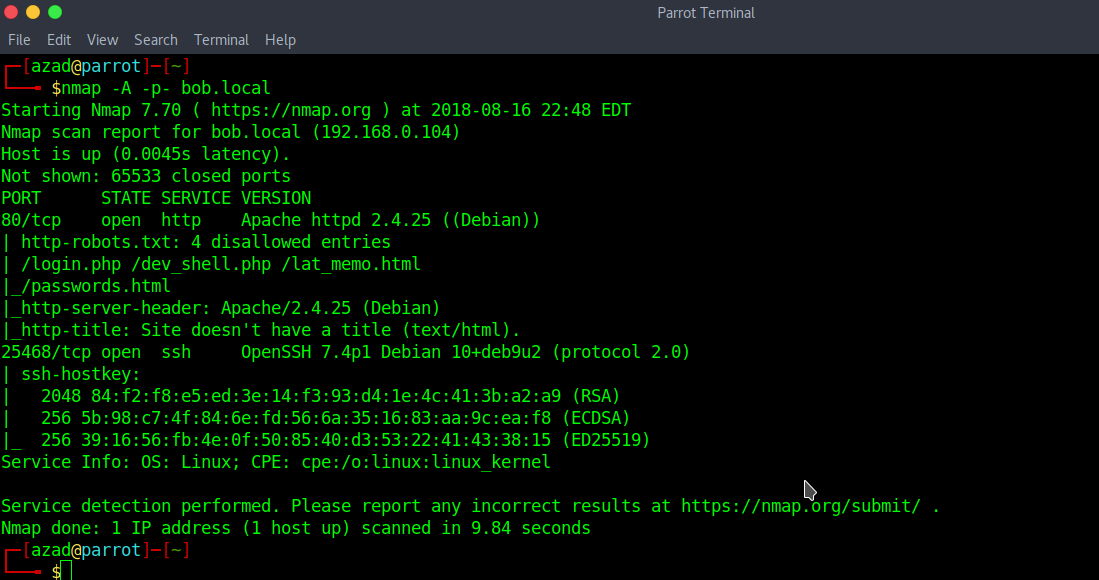
Zphisher | Zphisher is easier than Social Engineering Toolkit
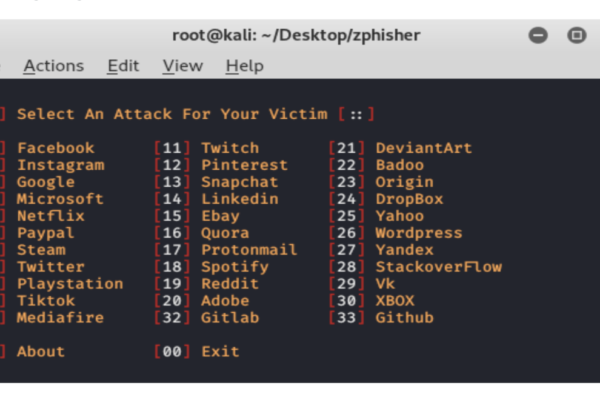
Zphisher – Automated Phishing Tool in Kali Linux Zphisher is a powerful open-source tool Phishing Tool. It became very popular nowadays that is used to do phishing attacks on Target. Zphisher is easier than Social Engineering Toolkit. It contains some templates generated by a tool called Zphisher and offers phishing template web pages for…