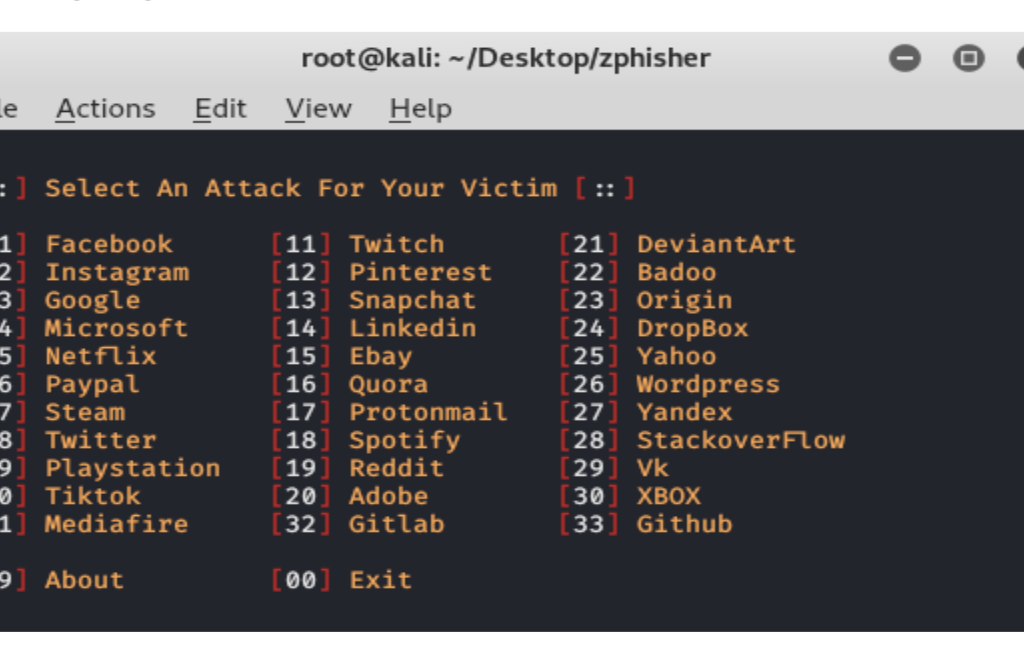
Zphisher | Zphisher is easier than Social Engineering Toolkit
Zphisher – Automated Phishing Tool in Kali Linux Zphisher is a powerful open-source tool…
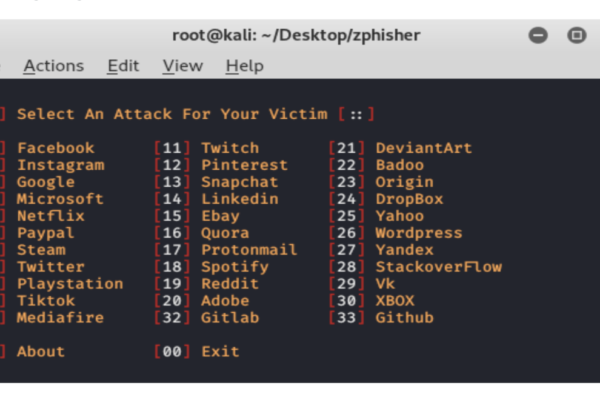
Zphisher – Automated Phishing Tool in Kali Linux Zphisher is a powerful open-source tool Phishing Tool. It became very popular nowadays that is used to do phishing attacks on Target. Zphisher is easier than Social Engineering Toolkit. It contains some templates generated by a tool called Zphisher and offers phishing template web pages for…

High Da Pa Backlink – Top 200 High DA PA Article Submission Sites List 2024 What is Off-page SEO? Activities performed off the website to raise its ranking in the Search Engine Results Page (SERPs) are referred to as off-page SEO. The foundation of off-page SEO is building backlinks. Backlinks serve as search engine indications for…
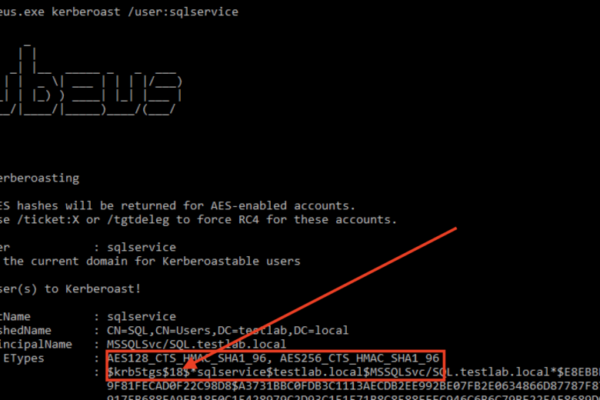
Introduction About Rubeus Rubeus is a C# toolkit designed to handle Kerberos interactions and breaches. It is well knowledge that Active Directories employ Kerberos, a ticket-based network authentication mechanism. Sadly, human mistake frequently results in AD configurations that do not prioritize security. In addition to creating keys and providing access with false certificates, Rubeus is…
Fake Hacking Screen Do you want to come off as a computer whiz and skilled hacker? When people witness anything they believe to be hacking, they are frequently impressed because hacking demands a high level of computer understanding. To give the impression that you are hacking, you don’t even need to break the law. All…

High DA PA DoFollow Backlink Submission Sites List 2023 Are you looking for a list of free high DA PA DoFollow sites to build high-quality backlinks and to grow organic traffic to your web pages in 2023? If yes, you are at the right source. DoFollow Backlinks plays a huge role in digital marketing to…

Twitter on Wednesday said that its investigation found “no evidence” that users’ data sold online was obtained by exploiting any security vulnerabilities in its systems. “Based on information and intel analyzed to investigate the issue, there is no evidence that the data being sold online was obtained by exploiting a vulnerability of Twitter systems,” the…
Mitigate the LastPass Attack Surface in Your Environment with this Free Tool The latest breach announced by LastPass is a major cause of concern for security stakeholders. As is often the case, we’re in a security quandary — on the one hand, as LastPass noted, users following LastPass best practices will be exposed to practically…
In this tutorial we will explore the Websploit Wifi Jammer module which we have edited to work with the latest version of Kali Linux. The Websploit Wifi Jammer module is a great tool to automatically disconnect every client connected to a targeted wireless network and access point. The WiFi jammer module also blocks new and…

September 2022 footage leak and rediit leakers seem to confirm that GTA 6 will initially be exclusive for PC and next-gen console.| GTA 6 possible release date The gaming world is eagerly waiting for any updates on Grand Theft Auto 6 from Rockstar. It’s been ten years since GTA 5 was released, but there has…

Threat actors leaked source code and gameplay videos of Grand Theft Auto 6 (GTA6) after they have allegedly breached Rockstar Game. The infamous September 2022 GTA6 leaks shocked the gaming industry, as Rockstar Games had no choice but to confirm them, thus revealing its most ambitious project yet. However, that hasn’t stopped the gaming studio…

Couple mistakenly given $10.5m from Crypto.com thought they had won contest, court hears. A Victorian woman accused of theft over a $10.5m mistaken cryptocurrency refund has been released on bail as she awaits trial, despite claims she allegedly tried to flee the country. | Cryptocurrency company Cryptocurrency trading platform Crypto.com accidentally transferred $10.5m to an…

[web_stories title=”true” excerpt=”false” author=”false” date=”false” archive_link=”true” archive_link_label=”” circle_size=”150″ sharp_corners=”false” image_alignment=”left” number_of_columns=”1″ number_of_stories=”5″ order=”DESC” orderby=”post_title” view=”circles” /]An EU Commission proposal to address child sexual abuse material online would make everyone less safe, including children, writes Callum Vogue. Callum Vogue is a Senior Government Affairs and Advocacy Advisor at the Internet Society. Governments across Europe are seeking…

It is the latest, most powerful, and best remote administration tool 2023 for android. You can hack up to thousands of android devices silently through this best android administration tool. It is a paid android rat but I provide you Cypher RAT v7 Latest Discount Link to buy this rat at a cheap price. It is…
Usage of WH-Cyberspace Hacking Tool for attacking targets without prior mutual consent is illegal. It’s the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program. Only use for educational purposes. WH-Cyberspace (Mr. Octopus) 🔞 Latest…

Promoting a local business directory isn’t easy these days. Whether it’s because of oversaturation or complicated search engine algorithms, it’s all too easy to feel like no one will be able to find your business in local search results. | Business Directories With exponential growth in “near-me” searches showing no signs of slowing down, getting…

Digital Forensics, Part 4: Finding Key Evidence in the Forensic Image In the previous articles in this series, we captured an forensic image of the suspect’s hard drive, we captured a forensic image of the suspect’s RAM and we had used Autopsy to recover deleted files from our first image. In this lab, we will…