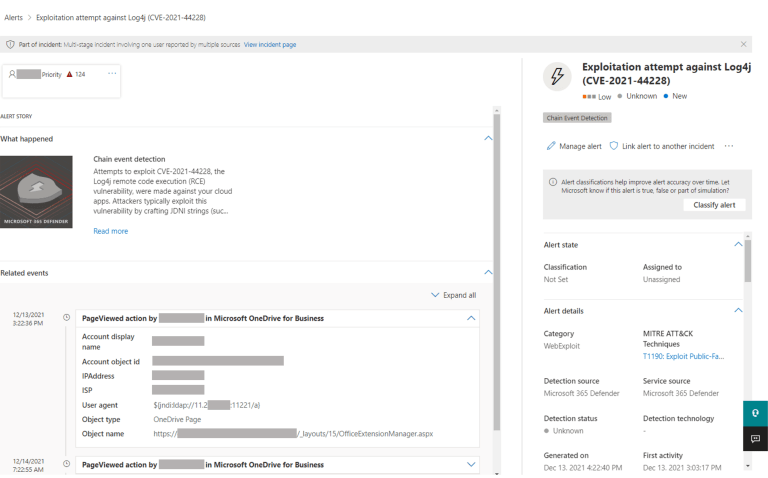
OpinionWorld Review 2022 | Earn Rewards With Online
Opinion world pays people to answer online surveys and give their honest opinions on a variety of topics, products and services. They are hired by businesses that want insight into their potential customer’s buying habits so that they can tailor their products to meet these needs. OpinionWorld is one of many survey sites that businesses…