Ah, the case of the missing WiFi password.This is a situation that many people have dealt with since the founding of WEP and WPA. The reasons for wanting to hack a Wi-Fi password can be different for all of us. Whether you forget it or want to share someone else’s network without your knowledge, learning how to hacking a WiFi password is an easy skill to get in and out of someone’s network.
However, it is important to pay attention before this. The process itself is relatively simple, but the actual act of doing it takes hours. That’s when it’s done correctly. What’s more, even if you do everything right, your computer and processing speed may not be fast enough to keep up and your Wi-Fi code may fail to crack. This process is long and not suitable for people in a hurry, so it may be easier to get free Wi-Fi from a coffee shop or other similar company. If you think you have what you need, or if you’re too far from the cafe to worry about, here’s how to hack your Wi-Fi password. | wifi hacking
I have assumed that most people living in Israel (and around the world) have insecure WiFi passwords. This password can be easily cracked or guessed by a curious neighbor or a malicious attacker.
My past experience, a relatively new WiFi attack described later, CyberArk Labs’ new monster cracking rig (8 x QUADRO RTX 8000 48GB GPU), and WiFi is everywhere because connectivity is more important than ever. A combination of facts I tried to find out if I was right with my hypothesis or just fortunate.
As the pandemic transition to remote work continues, protecting your home network becomes essential, or you risk your enterprise. Home networks rarely have the same controls as enterprise networks. And the security program is as powerful as its weakest link. | wifi hacking
Different Types of Wi-Fi
Before you start playing your hacker music in your head, take a step back to think about the type of Wi-Fi you’re hacking. Different types of Wi-Fi have different methods of protection, and so, different ways to crack them. Generally speaking, there are two types of security systems. The older version is a WPE. WPEs are a little easier to crack because they utilize older technology. The method of cracking this kind of network is also less aggressive, so it takes a little less time. | wifi hacking
On the other hand, you have WPAs WPA2 or WPA3, these types of network security models are the best in the market currently. They use more complex methods of protection and are really great at keeping intruders out. Unfortunately, that means a hacker like you has more trouble getting into the system. The method for cracking the code in this case is also more aggressive and labor-intensive for your computer. That leaves more chances for your own system to fail and shut down in the process. That being said, both methods are a bit tricky and require some level of patience to get through them. In this article, we’re going to take a look at how you can hack WPE, WPA, WPA2 and WPA3 networks.
Methods to Hack WiFi Password Successfully
Using WiFi Cracko application to Hack a Wi-Fi Password
The WiFi Cracko is an application for desktop and mobile devices built to find password of any wireless type of protection (WPA, WEP, WPA2-PSK) in just few minutes.
NEWS: In their newest update “v.1.3.0.” they released hacking of WPA3 type of security available as well.

This software is supported for both desktop PC and smartphone operating systems, including:
Microsoft Windows, MacOS, Android (.APK) and as an iOS (iPhone/iPad) App.
Users can download WiFi Cracko tool from its official website.
The app is very easy to use. All features are included inside its main interface start window where you just have to set the options according to a WLAN SSID which you’re interested to crack.
If you are not sure which type of security your adapter has enabled, the WiFi Cracko tool will automatically check it for you.
After few minutes of waiting the app to do its cracking process, a password will be shown in the buttom box where you can easily copy it for further use.
Using Kali Linux to Hack Wi-Fi Password
What You Need to Get Cracking
You probably know that hacking a Wi-Fi network can’t be done with just your PC or laptop alone. You need a bit of specialized equipment, as well as specific software to figure out the code. First things first, the Wi-Fi network you’re connecting with needs to be fast and utilized a lot. A faster and more active network is easier to hack because there’s a bigger transfer of information. This information is what your system needs to generate the code.
Next, you need a wireless adapter. You need an adapter that’s capable of packet injection. This packet injection is what your computer is going to use to add parts and sections into the network to make it look like the normal communications.
Recommended models are some of these (Google search for adapters below if you want to buy some of them, from eBay or Amazon or somewhere else:
– Alfa AWUS036NHA (2.4GHz)
– Alfa AWUS036H (2.4GHz)
– TP-Link WN722 (2.4GHz, first version only)
A big component of hacking in this case is the Kali Linux software (Official download page). This is available in a CD form, and is basically a system that allows your computer to test and configure passwords in various networks. It’s a security system of sorts, but also works against security systems.
Last but not least, you need a computer with a pretty fast processing speed. If your computer is slow, your process is going to be slow. The hacking time for this procedure takes long as it is, and a slow computer only elongates that time. Do yourself a favor and use a fast computer for this one. Once you have these key components, you’re ready to start hacking the Wi-Fi network.
How to Install Kali Linux
Before you can start, you need to install the Kali Linux system into your PC. As this is a large system, you need about 20 GB of disk space to install it, as well as a CD/DVD port in your computer. Download the Kali Linux software onto that CD or USB, so it becomes a live version. Also make sure that your computer is set to boot from inserting a CD or USB into it.
Once it’s on a physical copy, setting up your account is simple. Initially, you’re going to be asked to choose a name for your host system, as well as a password and time zone. After that, choose to set up an encrypted LVM for your Kali system. This allows you to transport the system on your CD or USB. Choose how you want your system to configure to your external drive.
Now, you’re going to be asked to create another password. This second password is for your external Kali boot. So, every time you use your external device to boot up and use your Kali system, this is the password you need to enter in. After this, you need to allow your external device to have a network mirror with the Kali system. This allows your version of the software to remain up to date with any additions or newer versions of the software. Along with that, install the GRUB booter to run your reboots of Kali smoothly.
Lastly, click ‘continue’ to reboot your Kali system. This is going to add the final touches to your device and the software overall to ensure smooth configuration between the two. If you’re using a USB drive, remember to enable boots from a USB device on your PC. Otherwise, your computer won’t be able to start up with Kali system. Now you’re Kali Linux is ready to get hacking.
Hacking a WPE Network
Assuming you’ve already installed the Kali Linux system, the first step for hacking is to start the program. Boot it up and open up a new terminal window to get started. This terminal window is where you’re going to enter commands for your system, resulting in different outcomes. Once you’ve opened up a new command window, grab a paper and pencil because you’re going to have to write a few key pieces of information.
Step 1: Gather Your Information
In the command box, type the text ifconfig. This command opens up the main information about your computer and wireless adapter. You should see a name for your system on the left-hand side. This is usually wlan0 or something similar. Note this text down, as it’s your interface name and is necessary to proceed.

Before you connect to a different Wi-Fi, you need to disconnect from your existing Wi-Fi. To do this, enter in airmon-ng check kill in the terminal box. This removes the Wi-Fi connection from your computer, and you won’t be able to connect to any network again unless you restart.

You can check that you’ve done this step correctly if after typing in airmon-ng check you see a blank text field.
Moving on, you need to collect information about the Wi-Fi network you want to hack, specifically the BBSID, or router information. Enter airodump-ng (interface) into the command box. You should see a pop up of all of the Wi-Fi networks nearby. Find the network name you’re interested in, and copy down the BBSID information about it.
Step 2: Begin the Crack
Now that you have all of the necessary information, it’s time to get cracking. After the previous step, your computer is going to be refreshing its results to show you nearby Wi-Fi networks. When you find the one you’re interested in, make sure to click (Ctrl+C) to stop refreshing and highlight a box. When you have the box of your desired Wi-Fi highlighted, enter reaver -i (interface) -b (BSSID) -vv -K 1 to start the hack. Fill in the interface and BBSID spaces with the corresponding values you found in the previous step.
This initiates Kali’s hacking feature, and it gets to work to try to find the password. This could take a few minutes or several depending on the complexity of the password. However, WPE Wi-Fi networks are easier to hack, so you might not have to wait long. If successful, you should see a pop up of a screen that says WPA PSK with a set of characters next to it. This is the password to the Wi-Fi network you’re looking for. You can now use to connect to that Wi-Fi source!
It’s also important to remember that someone else needs to be using the desired Wi-Fi network during the time of your hack for this to work. Without someone else using it, it becomes difficult for Kali to gather the necessary information and hack the system. This method works great for WPE-types because it’s less invasive, and WPE security systems are easier to breach. If you want to get into a WPA or WPA2 system, however, the next method is more suitable for you.
Hacking a WPA/WPA2 Network
This method is a bit more advanced and is likely to take a longer time. If you’re in a hurry, it’s probably best to just get a source of Wi-Fi from a free base because this is going to take hours. The beginning of the process is the same. We start with finding out information about your system.
Step 1: Find Your Information
Start by finding your computer’s wireless interface. Open new console and type in airmon-ng, and copy down the text you find in the box. Next, you to use the interface information to find latch on to the Wi-Fi network of your choice.

Type in airmon-ng start (interface), again, replacing the interface with the data you just collected. This should show you a list of the Wi-Fi sources near you. Click (Ctrl+C) to stop the page from refreshing and highlight the network you want. Note down the BBSID like last time, but also include the channel number for the network. Next, it’s time to make big moves by getting into the system.
Step 2: Find a Crack
In this step, you’re going to build a connection with the network you want, and then infiltrate the network’s system by appearing as a regular user. To do this, enter in airodump-ng –(channel) –(BSSID) -w /root/Desktop/ (interface) with the information you collected from before (channel, BSSID and interface should be replaced with information you gathered). This is going to create four separate files on your desktop that contain the ‘handshake’, or network connectivity via communication, information. This is what your computer and the network share to configure with each other.

Now, it’s time to enter the system. Type in aireplay-ng –0 2 –a (desired router BBSID) –c (your own BBSSID) mon0 into the command box, again, filling in the necessary information from your personal system. This is where the show begins. Kali then begins to send in information packets, building a connection with the new Wi-Fi system quickly. As it’s doing this, it appears to the other system that your computer is just a regular computer that uses the network often. By building the network configuration before, your computer can bypass a few of the systems set up that an outsider computer wouldn’t.
Step 3: Find the Password
After you’re in the network threshold, the last step of the process is to initiate a password or key search from the other Wi-Fi system. Do this by entering aircrack-ng –a2 -b (desired router BBSID) –w /root/wpa.txt /root/Desktop/*.cap in the text box. Watch as Kali begins to try different versions of the key until one fits the password. During this time, your screen is going to pop up with several different boxes, as Kali tries many different keys.
Once that’s complete, it’s time for you to sit back and relax. Your system and Kali Linux are going to do the rest. This is where WPA and WPA2 systems are trickier. These passwords are more unique and harder to crack, so it takes the Kali system longer to do its job. Essentially, the system uses brute force and hits the Wi-Fi network with key after possible key to get a match. This could take several hours depending on just how complex the password is. Eventually though, your system is going to find the key, and again, you can see it in the WPA PSK line. Now the Wi-Fi is yours to use!
Hacking Techniques
A typical hacker attack is not a simple, one-step procedure. It is rare that a hacker can get online or dial up on a remote computer and use only one method to gain full access. It is more likely that the attacker will need several techniques used in combination to bypass the many layers of protection standing between them and root administrative access. Therefore, as a security consultant or network administrator, you should be well versed in these occult techniques in order to thwart them. This chapter, which will be a review for advanced users, will introduce the main types of hacker attacks. Expert users will want to skip ahead to the next chapter (Chapter 7, “Wireless Attacks”) and go straight for the goodies. | wifi hacking
The following techniques are not specific to wireless networks. Each of these attacks can take multiple forms, and many can be targeted against both wired and wireless networks. When viewed holistically, your wireless network is just another potential hole for a hacker. Therefore, this chapter will review hacking techniques from a generic perspective. wifi hacking
Diverse Hacker Attack Methods
The stereotyped image conjured up by most people when they hear the term “hacker” is that of a pallid, atrophied recluse cloistered in a dank bedroom, whose spotted complexion is revealed only by the unearthly glare of a Linux box used for port scanning with Perl. This mirage might be set off by other imagined features, such as dusty stacks of Dungeons and Dragons lore from the 1980s, empty Jolt Cola cans, and Japanese techno music streaming from the Net.
However, although computer skill is central to a hacker’s profession, there are many additional facets that he must master. In fact, if all you can do is point and click, you are a script kiddie, not a hacker. A real hacker must also rely on physical and interpersonal skills such as social engineering and other “wet work” that involves human interaction. However, because most people have a false stereotype of hackers, they fail to realize that the person they are chatting with or talking to on the phone might in fact be a hacker in disguise. In fact, this common misunderstanding is one of the hackers’ greatest assets.
Social Engineering
Social engineering is not unique to hacking. In fact, many people use this type of trickery every day, both criminally and professionally. Whether it be haggling for a lower price on a lawn mower at a garage sale, or convincing your spouse you really need that new toy or outfit, you are manipulating the “target.” Although your motives might be benign, you are guilty of socially engineering the other party.
The Virtual Probe
One example of social engineering that information technology managers face on a weekly basis is solicitation from vendors. An inimical form of sales takes the form of thinly disguised telemarketing. Straying far from ethical standards of sales technique, such vendors will attempt to trick you into giving them information so they can put your company’s name on a mailing list.
Here is one such attempt that we get regularly:
“Hi, this is the copier repair company. We need to get the model of your copier for our service records. Can you get that for us?”
Now, this sounds innocent enough, and there are probably many that fall for this tactic. However, they are simply trying to trick you into providing sensitive information-information that they really have no business knowing.
Like the scam artist, a hacker often uses similar techniques. A popular method that hackers use is pretending to be a survey company. A hacker can call and ask all kinds of questions about the network operating systems, intrusion detection systems (IDSs), firewalls, and more in the guise of a researcher. If the hacker was really malicious, she could even offer a cash reward for the time it took for the network administrator to answer the questions. Unfortunately, most people fall for the bait and reveal sensitive network information.
Lost Password
One of the most common goals of a hacker is to obtain a valid user account and password. In fact, sometimes this is the only way a hacker can bypass security measures. If a company uses firewalls, intrusion detection systems, and more, a hacker will need to borrow a real account until he can obtain root access and set up a new account for himself. However, how can a hacker get this information? One of the easiest ways is to trick someone into giving it to them.
For example, many organizations use a virtual private network (VPN) that enables remote employees to connect to the network from home and essentially become a part of the local network. This is a very popular method of enabling people to work from home, but is also a potential weak spot in any security perimeter. As VPNs are set up and maintained by the IT department, hackers will often impersonate an actual employee and ask one of the IT staff for the password by pretending to have lost the settings. If the IT employee believes the person, he willingly and often gladly hands over the keys. Voila! The hacker now can connect from anywhere on the Internet and use an authorized account to work his way deeper into the network. Imagine if you were the lowly IT staff person on call and the CEO rang you up at 10:30 p.m. irate about a lost password. Would you want to deny her access, risking the loss of your job? Probably not, which makes this type of fear a hacker’s best friend.
Chatty Technicians
If you are a home user and think you have nothing to fear from this type of impersonation, think again-you are actually targeted more often by scammers and hackers alike. This is because many Internet newcomers (newbies) will believe anything someone appearing to be their ISP’s tech support personnel tells them. For example, hackers will often send out mass messages to people, or sit in chat rooms and wait for a newbie to come along. They will then set up a fake account or use simple tricks to make it appear as if an AOL employee is chatting with them. What the newbies do not realize is that they are actually talking with a hacker in disguise. So, they willingly hand over everything from credit cards to user names and passwords. See Figure 1 for an example of how a fake request might appear.
As you can see, to a beginner it appears that an AOL Administrator is on the other side of this conversation. However, if you look closely, you will see a blank like after Hckr-name:. To make it appear as though an AOL System Administrator is talking, we added a line of space characters to the beginning of the text to drop the AOL System Administrator: to the next line. Although the original name does appear, it would not be difficult for a hacker to set up an account using a date or company name to disguise the fact the account was simply another username.
Social Spying
Social spying is the process of “using observation to acquire information.” Although social engineering can provide a hacker with crucial information, small businesses are better protected against social engineering because many people in very small companies know each other. For example, if one of the IT staff received a call from a hacker pretending to be a distressed CEO, he would probably recognize the voice as not belonging to the real CEO. In this case, social spying becomes more important. | wifi hacking
To illustrate one of the nontechnical ways social spying can be used, consider how many people handle ATM cards. For example, do you hide your PIN when you take money out at the ATM? Take note of how people protect their PIN the next time you are in line at the ATM. You will probably note most people do not care. Most will whip out their card and punch the numbers without a care for who could be watching. If the wrong person memorized the PIN, he would have all the information needed to access the funds in the account, provided he could first get his hands on the ATM card. Thus, a purse-snatcher would not only get the money just withdrawn from an ATM, but could easily go back and withdraw the entire day’s limit. | wifi hacking
Similarly, hackers socially spy on users as they enter passwords. A “flower delivery” at 8:00 a.m. in the morning would give a hacker the necessary excuse to casually stroll through an office building. Although she appears to be looking for the recipient of the flowers, she could be watching for people entering passwords or other sensitive information. | wifi hacking
In addition to snooping on people as they actively type their user information, most offices have at least several people who are guilty of posting their password on or near their computer monitor. This type of blatant disregard for security is every network administrator’s worst nightmare. Regardless of repeated memos, personal visits, and warnings, some people seem to always find an excuse to post their network password right in plain view. Even if some people are at least security-conscious enough to hide their Post-it notes in a discreet place, it still only takes a few seconds to lift up a keyboard or pull open a desk drawer. | wifi hacking
If you do not believe this, take a quick walk around and see just how many potential security violations are in your office area. You might be very surprised to see just what type of information is there for the taking! | wifi hacking
Garbage Collecting
Have you ever thrown away a credit card statement without shredding it? If so, you are a potential target. Although you might consider your trash to be sacred territory that no one enters because it is dirty, your trash, and the trash of your company, is often a gold mine. Fishing through garbage to find passwords, also known as dumpster diving, can provide a hacker with the crucial information needed to take over your network. | wifi hacking
Let’s consider a scenario. If you are a network administrator and you receive an anonymous tip that people are posting passwords all around the office, what would you do? Most administrators would immediately investigate and send out a memo to everyone in the company stating that this activity is not allowed, and that violations will be dealt with harshly. Although this might get everyone to temporarily take down their Post-it passwords, the problem has only been exacerbated, for all those passwords are now headed right to the anonymous caller who is waiting at the dumpster. | wifi hacking
In addition to passwords, hackers can find memos, sensitive reports, diskettes, old hard drives, and more in the trash. Imagine the value an old cash register hard drive could have to a hacker looking for a way to gain access to a company’s credit card database. In many cases, a hard drive can simply be installed on another computer and searched using inexpensive (or free) forensics tools. | wifi hacking
Sniffing
A sniffer is a program and/or device that monitors all information passing through a computer network. It sniffs the data passing through the network off the wire and determines where the data is going, where it’s coming from, and what it is. In addition to these basic functions, sniffers might have extra features that enable them to filter a certain type of data, capture passwords, and more. Some sniffers (for example, the FBI’s controversial mass-monitoring tool Carnivore) can even rebuild files sent across a network, such as an email or Web page. | wifi hacking
A sniffer is one of the most important information gathering tools in a hacker’s arsenal. The sniffer gives the hacker a complete picture (network topology, IP addresses) of the data sent and received by the computer or network it is monitoring. This data includes, but is not limited to, all email messages, passwords, user names, and documents. With this information, a hacker can form a complete picture of the data traveling on a network, as well as capture important tidbits of data that can help her gain complete control over a network. | wifi hacking
How Does a Sniffer Work?
For a computer to have the capability to sniff a network, it must have a network card running in a special mode. This is called promiscuous mode, which means it can receive all the traffic sent across the network. A network card will normally only accept information that has been sent to its specific network address. This network address is properly known as the Media Access Control (MAC) address. You can find your own MAC address by going to the Windows Taskbar and clicking Start?Run and typing winipcfg (for Windows 95/98/ME) or ipconfig /all (for Windows NT/2000/.NET Server). The MAC address is also called the physical address. | wifi hacking
The only exception to this is what is called monitor mode. This type of network card status only applies to wireless network interface cards (NICs). Because of the unique properties of a wireless network, any data traveling through the airwaves is open to any device that is configured to listen. Although a card in promiscuous mode will work in wireless environments, there is no need for it to actually be part of the network. Instead, a WNIC can simply enter a listening status in which it is restricted from sending data out to the network. As you will learn later, a network card in promiscuous mode can be detected because of how it interacts with the network. Monitor mode stops all interaction. | wifi hacking
There are different layers involved in network communications. Normally, the Network layer is responsible for searching the packets of information for their destination address. This destination address is the MAC address of a computer. There is a unique MAC address for every network card in the world. Although you can change the address, the MAC address ensures that the data is delivered to the right computer. If a computer’s address does not match the address in the packet, the data is normally ignored. | wifi hacking
The reason a network card has this option to run in promiscuous mode is for troubleshooting purposes. Normally, a computer does not want or need information to be sent to other computers on the network. However, in the event that something goes wrong with the network wiring or hardware, it is important for a network technician to look inside the data traveling on the network to see what is causing the problem. For example, one common indication of a bad network card is when computers start to have a difficult time transferring data. This could be the result of information overload on the network wires. The flood of data would jam the network and stop any productive communication. After a technician plugs in a computer with the capability to examine the network, he would quickly pinpoint the origin of the corrupt data, and thus the location of the broken network card. He could then simply replace the bad card and everything would be back to normal. | wifi hacking
Another way to visualize a sniffer is to consider two different personality types at a cocktail party. One type is the person who listens and replies to conversations in which he is actively involved. This is how a network card is supposed to work on your local machine. It is supposed to listen and reply to information sent directly to it. | wifi hacking
On the other hand, there are those people at the party who stand quietly and listen to everyone’s conversation. This person could be compared to a network card running in promiscuous mode. Furthermore, if this eavesdropper listened for a specific subject only, she could be compared to a sniffer that captures all data related to passwords only. | wifi hacking
How Hackers Use Sniffers
Figure 2 shows a sniffer in action. As previously mentioned, sniffers like this are used every day to troubleshoot faulty equipment and monitor network traffic. Hackers can use this or similar tools to peer inside a network. However, they are not out to troubleshoot. Instead, they are out to glean passwords and other gems.
Depending on the program a hacker is using, he will get something that looks like Figure 2. As you can see from the figure, some data is easily readable, while some data is not. The difference is in the type of data that is sent. Computers can send information either in plain text or in an encrypted form. The sample capture shows just how easy it is to read captured plaintext data. | wifi hacking
Plaintext communication is any information that is sent just as it appears to the human eye. For most applications, this is the standard means of data transfer. For example, the Internet uses plaintext for most of its communications. This is the fastest way to send data. Chat programs, email, Web pages and a multitude of other programs send their information in plaintext. This is acceptable for most situations; however, it becomes a problem when transmitting sensitive information, such as a bank account number or a password. | wifi hacking
For example, take our sniffer screenshot in Figure 2. If you look closely at the plaintext section, you can see just how dangerous a sniffer can be to sensitive information. In the plaintext, you can see the following: Our company will be merging with another company. This will make our stock $$. Don’t tell anyone. If this were a real merger, a hacker could make millions overnight.
In addition, email clients and FTP clients do not normally encrypt their passwords; this makes them two of the most commonly sniffed programs on a network. Other commonly used programs such as Telnet, Web browsers, and news programs also send their passwords as plaintext. So, if a hacker successfully installs a sniffer on your network, he would soon have a list of passwords and user names that he could exploit. | wifi hacking
Even some encrypted passwords used in a Windows NT network can be sniffed. Thanks to the rather well-known encryption scheme of an NT password, it does not take long to capture and decrypt more than enough NT passwords to break a network wide open. In fact, there are even sniffing programs that have an NT password cracker built right into them. The programs are designed to be very user friendly so that network administrators can test their networks for weak passwords. Unfortunately, these programs often end up in the hands of script kiddies who can just as easily use them to cause problems. | hack wifi
Although sniffers most commonly show up within closed business networks, they can also be used throughout the Internet. As mentioned previously, the FBI has a program that will capture all the information both coming from and going to computers online. This tool, previously known as Carnivore, simply has to be plugged in and turned on. Although it is purported to filter out any information that is not the target’s, this tool actually captures everything traveling through whatever wire to which it is connected and then filters it according to the rules set up in the program. Thus, Carnivore can potentially capture all of those passwords, email messages, and chat sessions passing through its connection. | hack wifi
In addition to wired networks, sniffers can also be used in wireless networks. In effect, a wireless network on a corporate LAN is like putting an Ethernet jack in your parking lot. What makes this unique from a hacker’s perspective is that sniffing a wireless network is probably not illegal, although it has yet to be tested in court. In many ways, it is no different than a police scanner used by reporters and hobbyists worldwide. If the information is sent in plaintext to the public domain, how can it be wrong to simply listen? | wifi hacking
How to Detect a Sniffer
There are a few ways a network technician can detect a NIC running in promiscuous mode. One way is to physically check all the local computers for any sniffer devices or programs. There are also software detection programs that can scan networks for devices that are running sniffer programs (for example, AntiSniff). These scanner programs use different aspects of the Domain Name Service and TCP/IP components of a network system to detect any malicious programs or devices that are capturing packets (running in promiscuous mode). However, for the average home user, there is really no way to detect whether a computer out on the Internet is sniffing your information. This is why encryption is strongly recommended. | wifi hacking
How Can I Block Sniffers?
There is really only one way to protect your information from being sniffed: Use encryption! Using Secure Sockets Layer (SSL)-protected Web sites and other protection tools, you can encrypt your passwords, email messages and chat sessions. There are many programs available for free that are easy to use. Although you do not always need to protect the information passed during a chat session with your friends, you should at least have the option available when needed. | wifi hacking
Because of the very nature of a WLAN, encryption is a must in any situation. Fortunately, wireless networks come with the option of encryption built right into their software. However, few take advantage of this capability, as few are even aware that this option exists. | wifi hacking
Windows Commands to Get the Key
This trick works to recover a Wi-Fi network password (AKA network security key) only if you’ve previously attached to the Wi-Fi in question using that very password. In other words, it only works if you’ve forgotten a previously used password.
It works because Windows 8 and 10 create a profile of every Wi-Fi network to which you connect. If you tell Windows to forget the network, then it also forgets the password. In that case, this won’t work. But few people ever explicitly do that. | hack wifi
It requires that you go into a Windows Command Prompt with administrative privileges. Click the Star Menu, type “cmd” (no quotes), and the menu will show Command Prompt; right-click that entry and select Run as administrator. That’ll open the black box full of text with the prompt inside—it’s the line with a right-facing arrow at the end, probably something like C:\WINDOWS\system32\>. A blinking cursor will indicate where you type. Start with this:
The results will bring up a section called User Profiles—those are all the Wi-Fi networks (aka WLANs, or wireless local area networks) you’ve accessed and saved. Pick the one you want to get the password for, highlight it, and copy it. At the prompt below, type the following, but replace the Xs with the network name you copied; you only need the quotation marks if the network name has spaces in it, like “Cup o Jo Cafe.” | hack wifi
netsh wlan show profile name=”XXXXXXXX” key=clear
In the new data that comes up, look under Security Settings for the line Key Content. The word displayed is the Wi-Fi password/key you are missing.
On macOS, open up the Spotlight search (Cmd+Space) and type terminal to get the Mac equivalent of a command prompt. Type the following, replacing the Xs with the network name.
security find-generic-password -wa XXXXX
Reset the Router
This isn’t for getting on someone else’s Wi-Fi in the apartment next door. You need physical access to the router for this to work. But, before you do a full router reset simply to get on your own Wi-Fi, try to log into the router first. From there, you can easily reset your Wi-Fi password/key if you’ve forgotten it. | wifi hacking
That’s not possible if you don’t know the password for the router. (The Wi-Fi password and router password are not the same—unless you went out of your way to assign the same password to both). Resetting the router only works if you have access via Wi-Fi (which we’ve just established you don’t have) or physically, utilizing an Ethernet cable. | wifi hacking
If you’ve got a router that came from your internet service provider (ISP), check the stickers on the unit before a reset—the ISP might have printed the SSID and network security key right on the hardware. | hack wifi
Or use the nuclear option: Almost every router in existence has a recessed reset button. Push it with a pen or unfolded paperclip, hold it for about 10 seconds, and the router will reset to the factory settings.
Once a router is reset, you’ll need that other username/password combo to access the router itself. Again, do this via a PC attached to the router via Ethernet—resetting the router probably killed any potential Wi-Fi connection for the moment. The actual access is typically done with a web browser, though many routers and mesh systems now can be controlled via an app.
Some routers may also have a sticker with that default Wi-Fi network name (SSID) and network security key (password) so you can indeed go back on the Wi-Fi after a reset.
The URL to type into the browser to access a router’s settings is typically 192.168.1.1 or 192.168.0.1, or some variation. Try them randomly; that generally works. To determine which one on a PC connected to the router via Ethernet, open a command prompt and type ipconfig. Look among the gobbledygook for an IPv4 Address, which will start with 192.168. The other two spaces, called octets, are going to be different numbers between 0 and 255. Note the third octet (probably a 1 or 0). The fourth is specific to the PC you’re using to log into the router.
In the browser, type 192.168.x.1, replacing the X with the number you found in the ipconfig search. The 1 in the last octet should point at the router—it’s the number one device on the network. (For full details, read How to Access Your Wi-Fi Router’s Settings.) | wifi hacking
At this point, the router should then ask for that username and password (which, again, is probably not the same as the Wi-Fi SSID and network security key). Check your manual, assuming you didn’t throw it away, or go to RouterPasswords.com, which exists for one reason: to tell people the default username/password on every router ever created. You’ll need the router’s model number in some cases, but not all. | wifi hacking

You will quickly discern a pattern among router makers of utilizing the username of “admin” and a password of “password,” so feel free to try those first. Since most people are lazy and don’t change an assigned password, you could try those options even before hitting the reset button. (But c’mon, you’re better than that.) Once you’re in the Wi-Fi settings, turn on the wireless network(s) and assign strong-but-easy-to-recall passwords. After all, you don’t want to share with neighbors without your permission. | hack wifi
Make that Wi-Fi password easy to type on a mobile device, too. Nothing is more frustrating than trying to get a smartphone connected to Wi-Fi with some cryptic, impossible to key-in-via-thumbs nonsense, even if it is the most secure password you’ve ever created. | hack wifi
Crack the Code
You didn’t come here because the headline said “reset the router,” though. You want to know how to crack the password on a Wi-Fi network.
Searching on “wi-fi password hack,” or other variations, nets you a lot of links—mostly for software on sites where the adware and bots and scams pour like snake oil. The same goes for the many, many YouTube videos promising you ways to crack a password by visiting a certain website on your phone. | hack wifi
Download those programs or visit those sites at your own risk, knowing many are phishing scams at best. We recommend using a PC you can afford to mess up a bit if you go that route. When I tried it, multiple tools were thankfully outright deleted by my antivirus before I could even try to run the EXE installation file.
To test this hypothesis, I gathered 5,000 WiFi network hashes as my study group by strolling the streets in Tel Aviv with WiFi sniffing equipment. At the end of the research, I was able to break more than 70% of the sniffed WiFi networks passwords with relative ease. The Tel Aviv Metropolitan area has more than 3.9 million people — you can imagine what the numbers would have been had we not cut our research off at 5,000 WiFi networks. And while this research was conducted in Tel Aviv, the routers that were susceptible to this attack — from many of the world’s largest vendors — are used by households and businesses worldwide. | hack wifi
In this blog, I demonstrate how easily (you do not need a cracking rig) and with little equipment unsecure WiFi passwords can be cracked, thus hacking the WiFi network .At the end, we will reveal statistics of the cracked hashes and explain how to defend your network from this type of attack. Therefore, it is of utmost importance that we know and understand the cracking method to form an adequate defense. | wifi hacking
Let’s dig in
Before Jens “atom” Steube’s (Hashcat’s lead developer) research, when a hacker wanted to crack a WiFi password, they needed to capture a live four-way handshake between a client and a router occurring only during the establishment of the connection. Simply put, the attacker would need to be monitoring the network at the time the user or device connects to the WiFi network. Therefore, a hacker needed to be in a physical location between the access point (router) and the client, hoping that the user would enter the right password and that all four packets of the handshake were sniffed correctly. If a hacker did not want to wait until a victim establishes a connection (which can take hours, who connects to their home network while they are at work?), the attacker could de-authenticate an already-connected user to force the victim to have a new four-way handshake.
Another attack vector is to set up a malicious twin network with the same SSID (network name), hoping that the victim would try to log in to the fake network. A major shortcoming of this is, of course, that it is very noisy (meaning it can be easily traced) and can be easily noticed. | hack wifi
In simple English, if an adversary wanted to hack/crack a WiFi password, they need to be in the right place (between users and a router) at the right time (when users log in) and be lucky (users entered the correct password and all four packets were sniffed correctly). | hack wifi
All of this changed with atom’s groundbreaking research, which exposed a new vulnerability targeting RSN IE (Robust Security Network Information Element) to retrieve a PMKID hash (will be explained in a bit) that can be used to crack the target network password. PMKID is a hash that is used for roaming capabilities between APs. The legitimate use of PMKID is, however, of little relevance for the scope of this blog. Frankly, it makes little sense to enable it on routers for personal/private use (WPA2-personal), as usually there is no need for roaming in a personal network. | hack wifi
Atom’s technique is clientless, making the need to capture a user’s login in real time and the need for users to connect to the network at all obsolete. Furthermore, it only requires the attacker to capture a single frame and eliminate wrong passwords and malformed frames that are disturbing the cracking process.
Plainly put, we do not need to wait for people connecting to their routers for this attack to be successful. We are just in the vicinity of the router/network getting a PMKID hash and trying to crack it. | wifi hacking
To crack a PMKID, we first need to understand how it is generated.
How is PMKID hash generated and what elements does it contain

Figure 2- Flow of Calculating PMKID hash and PMK
The hash calculation might seem daunting at first glance but let us dive into it.
We need to generate a PMK driven from SSID (the network name) and the Passphrase; then we generate a PMKID driven from the PMK we generated, the AP MAC address, and the client MAC address. So let us see where we can find those:
The PMK is computed as follows:
![]()
Figure 3- PMK calculation
- Passphrase– The WiFi password — hence, the part that we are really looking for.
- SSID – The name of the network. It is freely available at the router beacons (Figure 3).
- 4096 – Number of PBKDF2 iterations
![]()
Figure 4 – SSID from a beacon
After a PMK was generated, we can generate a PMKID.
The PMKID is computed as follows:
![]()
Figure 5 – PMKID calculation
- PMK – What we are searching for, generated above. In WPA2 personal, the PMK is the PSK (will be explained in the next paragraph).
- “PMK Name” – Static string for all PKMIDs.
- MAC_AP – Access Point’s MAC address – This address can be found in any frame send by the router (Figure 4).
- MAC_STA – The client’s Mac address can be found in any frame sent by the client’s computer(Figure 4). It can moreover be found in the output of ifconfig\ip a commands.
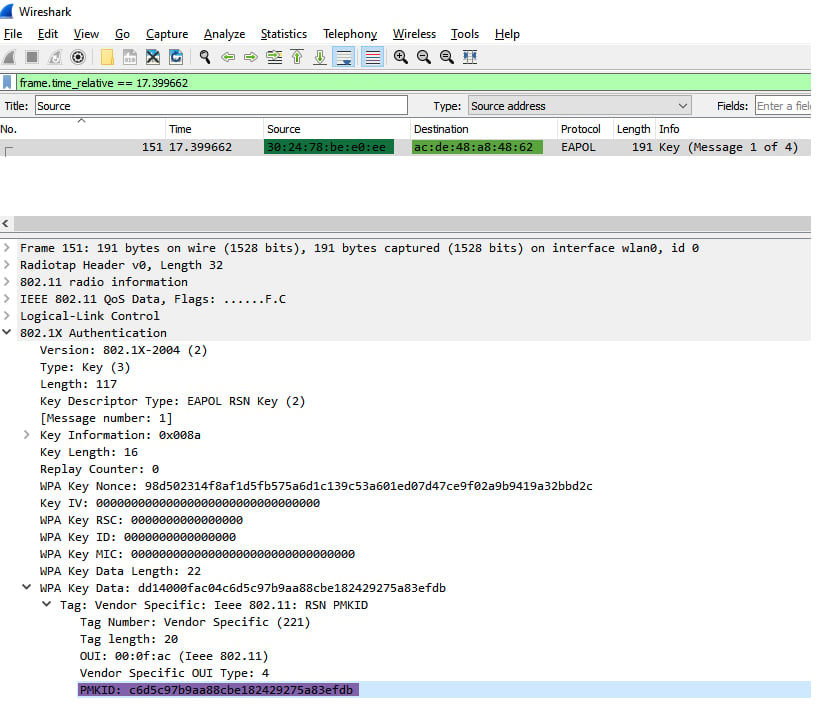 Figure 6 – PMKID, AP’s MAC, Client’s MAC
Figure 6 – PMKID, AP’s MAC, Client’s MAC
Cracking the PMKID hash is ultimately just generating/calculating PMKs with the SSID and different passphrases, then calculating PMKID from the PMK and the other information we obtained. Once we generated a PMKID equal to the PMKID that was retrieved from the AP (Figure 3), the hash is cracked; the passphrases that were used to generate the right PMK that the PMKID was generated from is the correct WiFi password. | wifi hacking
Now we know how a PMKID is being generated, and we can continue to the sniffing and cracking phases of our research.
Sniffing PMKID
To gather WiFi PMKID hashes, a wireless network interface that has monitor mode capabilities is required. Monitor mode allows packet capturing without having to associate with an access point.
I bought an AWUS036ACH ALFA Network card for $50 (there are even cheaper options) that supports monitor mode and packet injection and went around the center of Tel Aviv to sniff WiFis.
Before we can start the sniffing, we need to prepare our environment:
I used an ubuntu machine with AWUS036ACH ALFA.

Figure 7 – AWUS036ACH ALFA NIC
We build the package Hcxdumptool — a great utility by ZerBea to capture packets from WLAN devices.
After that, we need to install drivers with monitor mode capability. Each chipset has its drivers:
It is recommended to shut down services that might interfere with Hcxdumptool execution:
Then it is time to start sniffing. Hcxdumptool is a powerful tool that can be used for various attacks, not only the PMKID; therefore, we disable any attack that is not targeting PMKID.
- -i my Alfa NIC, you can execute ifconfig\ip a to find your interface name.
- -o the output pcapng of the execution.
Now wear a hoody, because you will get a PMKID of every network you cross by that is vulnerable to the attack.

Figure 8 – Me in a hoodie
When I reached 5,000 collected networks, I decided to quit; Israeli summer was too hot for me, so I turned to the fun part — cracking.
It’s cracking time!
Our first step in the cracking procedure is to install hashcat, the world’s fastest and most advanced password recovery tool. As the sniffing results are in the form of pcapng, we needed to convert them into a hashfile format to fit it to hashcat. For this goal, I made use of another tool from the great suite of hcxtools.
Resulting in a hashfile that each line takes on the following structure:
SIGNATURE*TYPE*PMKID/MIC*MACAP*MACSTA*ESSID* * *
Here is an example of a hashline:
WPA*01*c6d5c97b9aa88cbe182429275a83efdb*302478bee0ee*acde48a84862*54686557494649***
- SIGNATURE = “WPA”
- TYPE = 01 for PMKID, 02 for EAPOL, others to follow
- PMKID/MIC = PMKID if TYPE==01, MIC if TYPE==02
- MACAP = MAC of AP
- MACSTA = MAC of station
- ESSID = ESSID
- Not used in a PMKID attack:
- ANONCE = ANONCE
- EAPOL = EAPOL (SNONCE is in here)
- MESSAGEPAIR = Bitmask
The next step is to commence the cracking procedure by executing hashcat: | wifi hacking
Hashcat’s capabilities include several cracking methods, of which the most common are dictionary + rules and mask attack. The methods differ in the way they are forming the Passphrase.
We chose to start with what’s called a “mask attack,” due to the terrible habit many people living in Israel have of using their cellphone numbers as WiFi passwords. You can think of mask attack as Regex:
- ?d – digits
- ?l – lower case characters
- ?u – Upper case characters
- ?s – special symbols as ? ! $ …..
The mask for the password: 202!$ummeR would become ?d?d?d?s?s?l?l?l?l?u
Here is my Hashcat command that tried all the possible cellphone numbers combinations in Israel [the Israeli cellphone prefix is 05]
During this first execution of the mask attack, we cracked 2,200 passwords. Let’s calculate the number of options for Israeli cellphone numbers:
It is 10 digits long and it starts with 05. Therefore, we need to guess the remaining 8 digits.
Each digit has 10 options (0-9), hence 10**8 possible combinations. One hundred million seems like a lot of combinations, but our monster rig calculates at the speed of 6819.8 kH/s which translates into 6,819,000 hashes per second.
A cracking rig is not required as my laptop can get to 194.4 kH/s, which translates into 194,000 hashes per second. That equals more than enough computing power to cycle through the possibilities necessary to crack the passwords. Consequently, it took my laptop roughly 9 minutes to break a single WiFi password with the characteristics of a cellphone number. (10**8)/194,000 = ~516 (seconds)/60 = ~9 minutes.
The cracking speed for hashtypes differs because of different hash functions and the number of iterations. For example, PMKID is very slow compared to MD5 or NTLM. Nonetheless, it is feasible to crack a PMKID hash if the attacker focuses on a specific network, and the password is not complicated enough.
Afterward, we executed a standard dictionary attack with the most common dictionary, Rockyou.txt, and cracked more than 900 hashes. Here is a small glimpse into Rockyou.txt content:
123456 12345 123456789 password iloveyou princess 1234567 rockyou 12345678 abc123 nicole daniel babygirl monkey lovely jessica 654321 michael ashley
Let’s look over the statistics of the cracked hashes:
Cracked passwords by their length:
| Password Length | Occurrences |
| 10 | 2405 |
| 8 | 744 |
| 9 | 368 |
| 12 | 14 |
| 11 | 14 |
| 14 | 7 |
| 13 | 7 |
| Sum | 3,559 |
As you can see, except for the 10-digit password — which we had a tailored mask for — as the password length increased, the number of cracked passwords decreased. The lesson here? The longer the password, the better. | hack wifi
Top 4 masks for the cracked passwords:
| Mask | Occurrences | Meaning |
| Mask | Occurrences | Meaning |
| ?d?d?d?d?d?d?d?d?d?d | 2349 | 10 digits |
| ?d?d?d?d?d?d?d?d | 596 | 8 digits |
| ?d?d?d?d?d?d?d?d?d | 368 | 9 digits |
| ?l?l?l?l?l?l?l?l | 320 | 8 lower case letters |
| Sum | 3,633 |
We can see that cracked passwords most often fit a mask that contains only digits or only lower-case characters.
Not all routers support roaming features and are, therefore, not vulnerable to the PMKID attack. However, our research found that routers manufactured by many of the world’s largest vendors are vulnerable. | hack wifi
As I estimated beforehand, the process of sniffing WiFis and the subsequent cracking procedures was a very accessible undertaking in terms of equipment, costs and execution.
The bottom line is that in a couple of hours and with approximately $50, your neighbor or a malicious actor can compromise your privacy and much more if you don’t have a strong password.
Important Notes
There are a few important things that should be mentioned here. During the time of hacking, your computer may experience an overload of processing. This causes the hack to fail and results in the system starting over again. Though your system is likely to restart on its own and continue the process without any prompting from you, it’s still going to take much longer than a single boot. Even if you have a fast processor, it just depends on the situation to see how successful you are, as information rates between the two networks fluctuate.
Secondly, while this may be out of your control, the system you’re hacking needs to be a strong Wi-Fi network. A weak network signal is harder for your system to catch on to. Kali Linux needs a strong signal to inject the data packets and collect the necessary information. A system that’s too far away from your location or just generally weaker is going to result in either frequent shut downs or just a very, very slow process.
Conclusion
In total, we cracked more than 3,500 WiFi network in and around Tel Aviv – 70% of our sample.
The threat of a compromised WiFi network presents serious risk to individuals, small business owners and enterprises alike. And as we’ve shown, when an attacker can crack more than 70% of WiFi networks in a major global city with relative ease, greater attention must be paid to protecting oneself.
At the most basic level, people who use your network take part of your bandwidth, which may slow down your internet experience. However, more consequential is that once attackers gain access to your network, they can launch various man-in-the-middle (MITM) attacks. That can lead to attackers gaining access to your important accounts, such as your bank account, your email account (which is everything in modern life) and compromising other sensitive credentials. This also further opens attack vectors to your IoT devices like smart home equipment, smart TVs, security systems, etc. | wifi hacking
For the small business, the risk lies in an attacker infiltrating a network and then moving laterally to high-value applications or data, such as a billing system or cashier.
Concerning the enterprise, it’s possible for an attacker to gain initial access to a remote user’s WiFi and then hop to the user’s computer and wait for a VPN connection or for the user to go to the office and move laterally from there. | wifi hacking
From a broader perspective, computers and other devices are usually not accessible from outside of the network because of NAT, but once an attacker is in the network, it facilitates a range of attack vectors.
How should I protect myself?
- Choose a complex password. A strong password should include at least one lower case character, one upper case character, one symbol, one digit. It should be at least 10 characters long. It should be easily remembered and hard to anticipate. Bad example: Summer$021
- Change the default username and password of your router.
- Update your router firmware version.
- Disable weak encryption protocols (as WAP or WAP1).
- Disable WPS.
It’s important to note that implementing multi-factor authentication (MFA) for personal WiFi is difficult and largely impractical for a personal WiFi and a non-technical consumer. It is also unlikely that MFA will be widely available for general consumer use cases in the near feature. | wifi hacking
I would like to give a big shout-out to Atom and ZerBea for their incredible work on this attack technique and for their work in general. | wifi hacking
I hope you enjoyed this blog and that you will take the required steps to secure your WiFi network. And as a reminder, none of the passwords we cracked were used for unauthorized access to these WiFi networks or any other information accessible via these networks. | wifi hacking