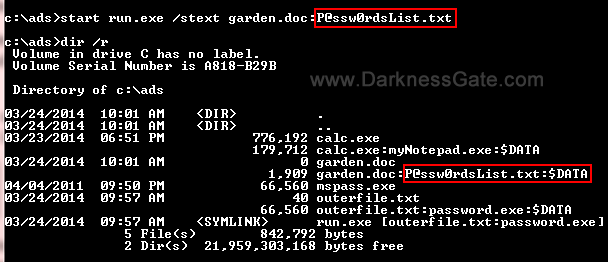
Apple drops controversial lawsuit against Corellium
Apple has dropped a controversial intellectual property lawsuit against virtualization software maker Corelium, days before the case was set to go to trial. Corelium’s software technology enables users to create virtual iOS devices within a browser, allowing security researchers to more easily test for bugs and exploits. The same virtualization technology allows tech journalists to…