
- Version 1.1
- Download 777
- File Size 4.5 MB
- Create Date June 29, 2020
- Download
One of the most prevalent forms of waste and fraud in today's digital advertising ecosystem is botnets. A Athena botnet is a network of computers infected with malware and controlled without the user being aware, typically for nefarious activities including various forms of digital advertising fraud.
To share some additional information with you about how botnets are used to create invalid traffic and ad impressions, let's take a deeper look at the Athena botnet Like other Botnet codebases, the Athena software was developed to control and manage the collection of hacked machines. In September 2013, the widely used Athena codebase was leaked. Security vendors quickly elaborated the internal workings of botnets (e.g., see here and here). However, because none of the write-ups discussed the Impression Fraud module, which were included in the codebase, I wanted to take the opportunity to fill that knowledge gap. Beyond its availability, Athena was chosen as a good example of a perception fraud threat that can easily be avoided by methods such as observable checking and IP blacklists.
Athena has two primary components: 1) infection software that connects victims with botnet commands and control channels, and 2) a management interface to direct infected machines. Athena does not oppose the delivery code or the exploitative code. It supplies the bus control mechanism after the machines are infected. A botnet is a collection of infected machines reporting a given URL. HTTP-based communication includes initial bot setup, bot status update, and dispatch functions. In addition to maintaining bots, the command and control machine hosts a web portal that allows the botmaster to direct the botnet.
I created a laboratory environment to study the behavior of Athena's advertising fraud mechanism. To do this, the LAMP stack was installed on the command and control boxes, the management panel was copied to / var / www, and Athena's setup scripts configured the database. Accessing http: // localhost / login verifies that the portal was functioning correctly. The next step was to make windows executable that connects machines to botnets. The Athena Builder program accepts several parameters (one of which is the URL of the command and control machine) and outputs an exploit executable. The final stage is recruiting victim machines in the botnet. This is as simple as running an executable on a collection of Windows installations. The exploit process removes the executable and after a while that will appear in the machine portal's ballist. After a few hours of work, a botnet is assembled and ready for experiments.
Boatmaster's management interface provides functionality similar to other modern management interfaces, including user experience and an effort for human factor engineering. Without this technical expertise, Botmaster can control every aspect of the botnet with this interface. For example, the management interface supports multiple accounts for each with its own set of permissions. It reports real-time data about the state of the botnet. Botmasters can use the interface to manage the queue of commands that will be accessed to the drone to execute. The UI also enables command execution progress to be tracked.
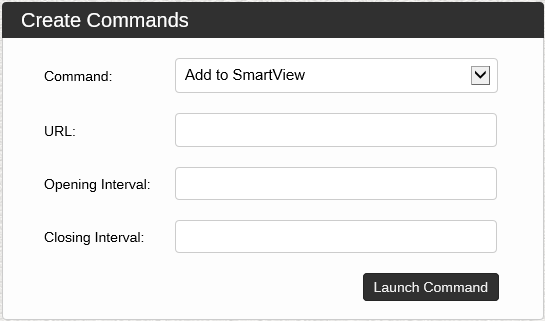
Issuing commands to the botnet is accomplished using the "create command" page. Each command has a set of specific parameters. For example, the Download & Execute command contains a URL parameter that requires the specification of the URL of the code to run. Finally, the filter section is used to specify which bots will be issued the command. This allows the command to be sent to a subset of the bot that satisfies a defined set of requirements. I will focus on ad-specific commands, but here is a full list of commands (note that denial-of-service commands are distributed)
The first two impressions are fraud commands view and view hidden. This has similar results except for their presence on infected machines. The view command will open an Internet Explorer instance (even if the second browser is the default) and browse to the given URL. Hidden View also uses Internet Explorer to load URLs, but the example of Internet Explorer is hidden from the desktop (and users of the infected machine). This allows Botnet to load webpages without the risk of indicating an infection with unexpected browser windows. After the view command is created, it is entered in the queue of the active command. The next time each bot phone is at home, the bot will receive the command and immediately see the specified URL once. This is the effect of running a reluctant audience of infected machines in the URL of the botmaster's selection.
SmartView is an incremental refinement to the view hidden command. This adds randomness to the opening and closing of the hidden window. This requires two parameters that specify how long to wait before opening the URL and how long to keep the page open sequentially. After the command is issued, the bot selects a random number until the opening interval and waits for several seconds before viewing the page. Similarly, the bot selects a random number up to the closing interval to determine whether to keep the page open. This impression allows the ideas to display a bit more "organic" and better mimic human behavior, as each bot's page is open in a slightly different period.
The distributed nature of Athena combined with the use of local browser instances makes it a formidable threat to standard visibility detection methods. Since the IP addresses of bogus views of the source are derived from live but infected machines in the botnet, the effectiveness of the IP blacklist will be limited. In addition, the installation of an infected user of Internet Explorer is used, including the user's history, cookies, and profile. This means that a user with a long history of conversions and a well-defined profile may inadvertently drive fraudulent views along with their normal Internet usage. The implication is that many different versions of Internet Explorer and plug-in configurations will appear on URLs targeting simple user agent filter ineffective. Finally, the views given from Athena Botnet are 100% viewable. The page geometry calculation shows any above the fold impressions within the browser viewport and viewable.









I enjoyed your article. You’re a skilled writer
and I read your stuff fairly often and you’re always
publishing interesting blogs.
Continue on with the great content pal!
how to write a phd thesis thesis topics in education
thesis assistance thesis literature review