Hello Friends I am Jdsingh
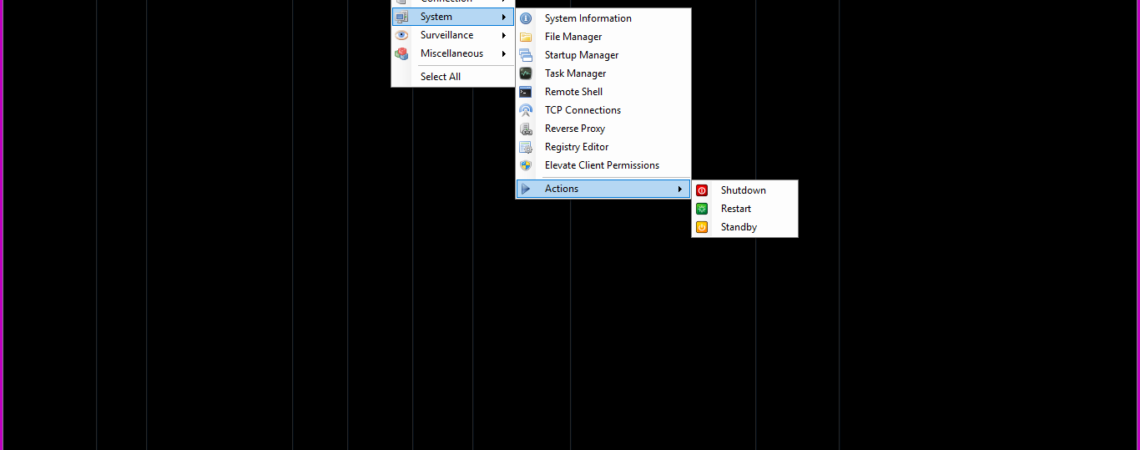
What Is Rat (Remote Administration Tool)..?
A remote administration tool (RAT) is a piece of software that allows a remote “operator” to control a system as if he has physical access to that system. While desktop sharing and remote administration have many legal uses, “RAT” software is usually associated with criminal or malicious activity. Malicious RAT software is typically installed without the victim’s knowledge, often as payload of a Trojan horse, and will try to hide its operation from the victim and from security software.
How Do Rats Work..?
Many trojans and backdoors now have remote administration capabilities allowing an individual to control the victim’s computer. Many times, a file (often called a client or stub) must be opened on the victim’s computer before the hacker can have access to it. These are generally sent through email, P2P file sharing software, and in internet downloads. They are usually disguised as a legitimate program or file. Many clients/stubs will display a Fake error message when opened, to make it seem like it didn’t open. Some will also disable antivirus and firewall software.
Functions of a Rat..?
- Screen/camera capture or image control
- File management (download/upload/execute/etc.)
- Shell control (from command prompt)
- Computer control (power off/on/log off if remote feature is supported)
- Registry management (query/add/delete/modify)
- Hardware Destroyer (overclocker)
- Other software product-specific functions
- Block mouses and keyboards
- Change the desktop wallpapers
- Downloads, uploads, deletes, and rename files
- Destroys hardware by overclocking
- Drop viruses and worms
- Edit Registry
- Use your internet connection to perform denial of service attacks (DoS)
- Format drives
- Steal passwords, credit card numbers
- Alter your web browser’s homepage
- Hide desktop icons, task bar and files
- Silently install applications
- Log keystrokes, keystroke capture software
- Open CD-ROM tray
- Overload the RAM/ROM drive
- Send message boxes
- Play sounds
- Control mouse or keyboard
- Record sound with a connected microphone
- Record video with a connected webcam
- Show fake errors
- Shutdown, restart, log-off, shut down monitor
- Record and control victim’s screen remotely
- View, kill, and start tasks in task manager
- Let the hacker surf the web with the IP-address of the infected computer
https://en.wikipedia.org/wiki/Njrat










Today, I went to the beachfront with my kids. I found a sea shell and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She put the shell to her ear and screamed. There was a hermit crab inside and it pinched her ear. She never wants to go back! LoL I know this is entirely off topic but I had to tell someone!
Hi my loved one! I want to say that this article is awesome, nice written and come with approximately all significant infos. I would like to see extra posts like this .
thanks bro
My husband and i have been peaceful that Albert managed to carry out his web research through the entire ideas he obtained when using the web site. It is now and again perplexing just to continually be giving freely tips that the others could have been trying to sell. So we understand we now have you to thank for that. The most important illustrations you’ve made, the straightforward site menu, the friendships your site aid to promote – it is most awesome, and it is facilitating our son in addition to the family do think the idea is entertaining, which is wonderfully pressing. Thanks for all the pieces!
Whats up! I just wish to give an enormous thumbs up for the great data you have here on this post. I will be coming again to your weblog for more soon.
Kitapyurdu Kitap Al En Popüler Kitaplar 2015