Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet to perform many hacks, Metasploit. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, installing keylogger and remotely turning on a webcam. We are also able to save the world from nuclear destruction, see if our girlfriend is cheating, spy on suspicious neighbors, avoid antivirus detection, and more.
In each of those tutorials, we focused primarily on using two types of Metasploit modules, exploits and payloads, but Metasploit has many other types including NOP (no operations), encoder, post (post exploit) and helper . In this article, I want to introduce you to the helpful modules in Metasploit where many powerful tools await our call.
[the_ad_placement id=”singh”]
Fire Up Kali
Let’s get started. First, fire Kali and open a terminal like the one below.
[the_ad id=”1250″]
Go to Metasploit Framework Directory
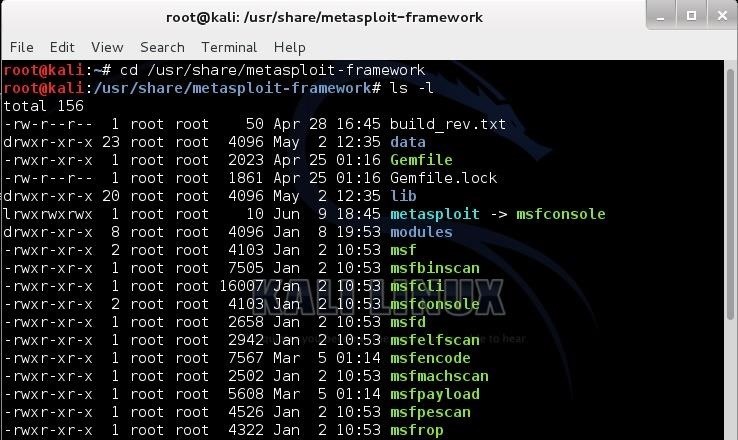
Now, let’s navigate to the Metasploit directory in Kali:
cd /usr/share/metasploit-framework
Please note that we are not implementing the Metasploit console. We are just navigating to where Metasploit resides in the file system, so that we can find out what modules exist there.
Next, let’s list the contents of that directory like that below.
kali > ls -l
[the_ad_placement id=”singh”]
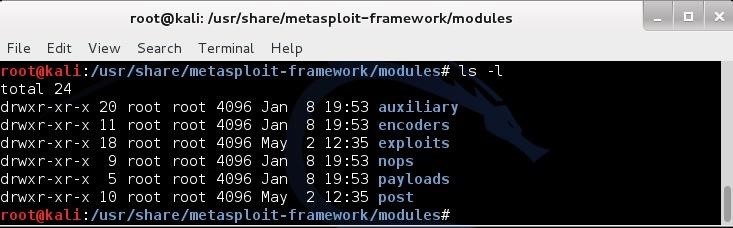
Let’s now navigate to the subdirectory modules and do a listing on that subdirectory.
kali > cd modules
kali > ls -l
As we can see in the screenshot above, Metasploit has six (6) different types of modules:
- auxiliary
- encoders
- exploits
- nops
- payloads
- post
As stated before, in nearly every previous Meatsploit tutorial here on Null Byte, we have focused exclusively on the exploits and payloads. I have also done a couple of guides on using the encoders module, but we have never explored the NOPs, auxiliary, or post modules. Today, let’s examine what is available to us in the auxiliary module.
[the_ad id=”1250″]
Open Auxiliary Directory
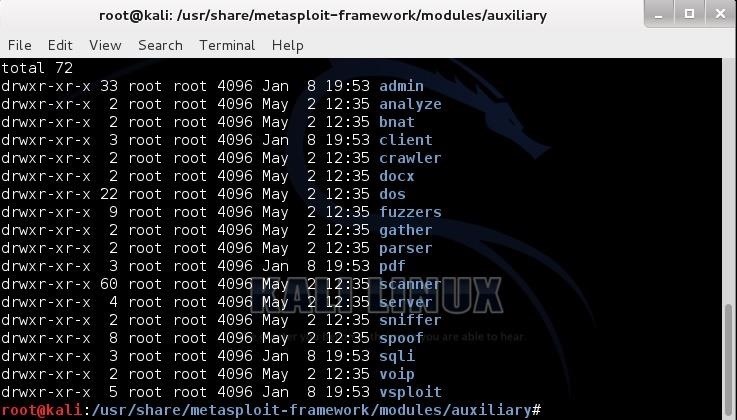
First, let change directories to the auxiliary directory and do a directory listing.
kali > cd auxiliary
kali > ls -l
When we do so, we can see that the auxiliary module directory is broken down to many sub-directories starting with the admin directory and ending through the vspoit directory.
[the_ad id=”1250″]
Explore the Auxiliary Sub Directories
As you can see, there are numerous auxiliary directories and modules, but for now, let’s focus on one—the fuzzers.
Fuzzing
Fuzzing is the practice of attempting random input into a variable area to see whether we can “break” it. That is, if we try to put too much data or a data of a type not expected, we may be able to get the buffer to overflow.
Buffer overflows (I’ll do a few articles soon on this subject) are among the most serious types of vulnerabilities as they often enable us to execute our own code remotely. Fuzzing is often the first step in finding a vulnerability that may lead to the development of a zero-day exploit.
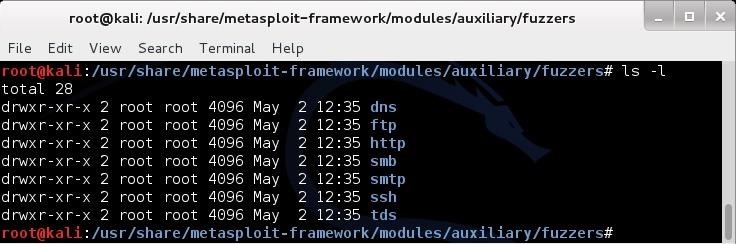
Now let’s navigate to the fuzzer directory:
kali > cd fuzzers
Once we are in the fuzzer directory, let’s look inside with an long listing.
kali > ls -l
As you can see, Metasploit has seven (7) types of fuzzers:
- dns
- ftp
- http
- smb
- smtp
- ssh
- tds
Each of these directories include programs or scripts that enable us to fuzz a particular protocol or function. We will focus our attention on ftp fuzzing in this tutorial.
[the_ad id=”1250″]
Open the Fuzzers
Let’s look inside the ftp fuzzing directory:
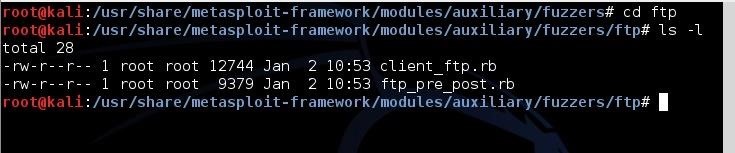
kali > cd ftp
kali > ls -l
As you can see, there are two fuzzers for ftp, the client_ft.rb and the ftp_pre_post.rb. Let’s use the ftp_pre_post.
Use the FTP Pre Post Fuzzer
Now that we have identified an auxiliary module we want to use, let’s open the msfconsole and find and use this module. Open the msfconsole by typing msfconsole in any directory from a terminal. This will open up the msfconsole and provide us with an msf prompt.
To find the fuzzer modules in Metasploit, we can use the search function built into msfconsole. We can type:
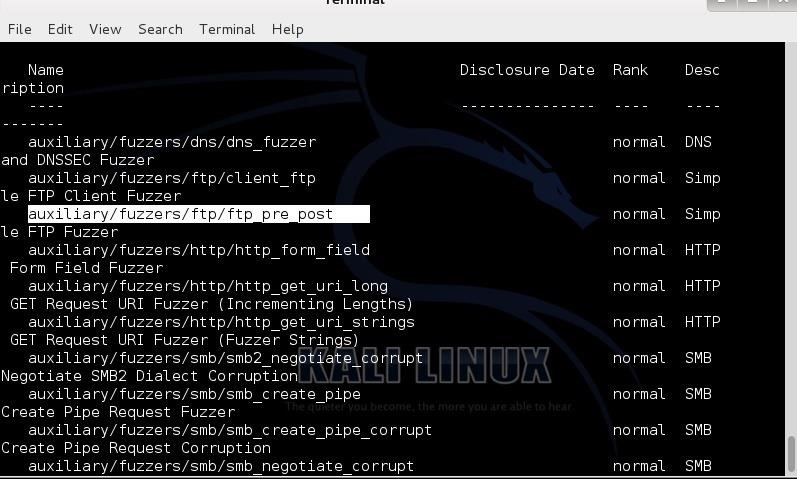
msf > search type:auxiliary fuzzers
Here we are asking msfconsole to list us only those modules that are auxiliary (type:auxiliary) and contain the keyword, ftp.
The results of that search are listed above. I have highlighted in the screenshot the module we will be using, auxiliary/fuzzers/ftp/ftp_pre_post.
[the_ad_placement id=”singh”]
Load the Fuzzer Module
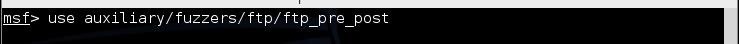
To load the module, simply type:
msf > use auxiliary/fuzzers/ftp/ftp_pre_post
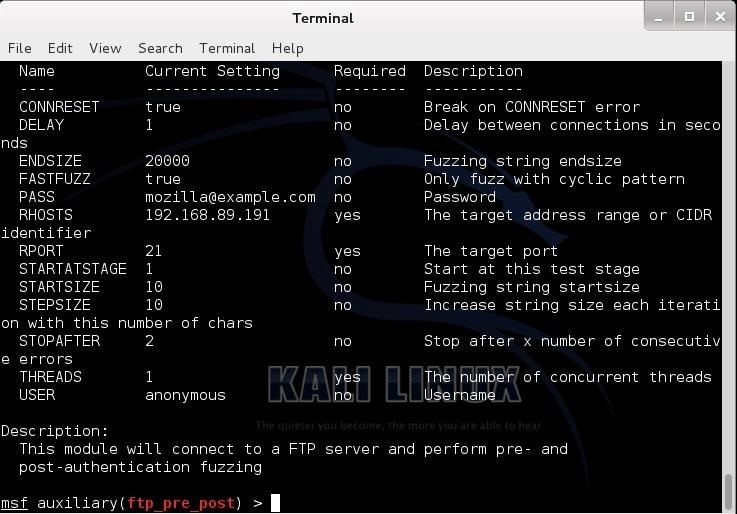
Let’s take a look at the particulars of this module by looking at its info page.
msf > info
Although this module has many options, to run it we only need to provide a target IP address. In this case, we will run it against a Windows 2003 server with IIS 6.0 and an FTP server. Let’s set the IP address:
msf > set RHOSTS 192.168.1.1
After setting the target IP address, we then only need to run this ruby script.
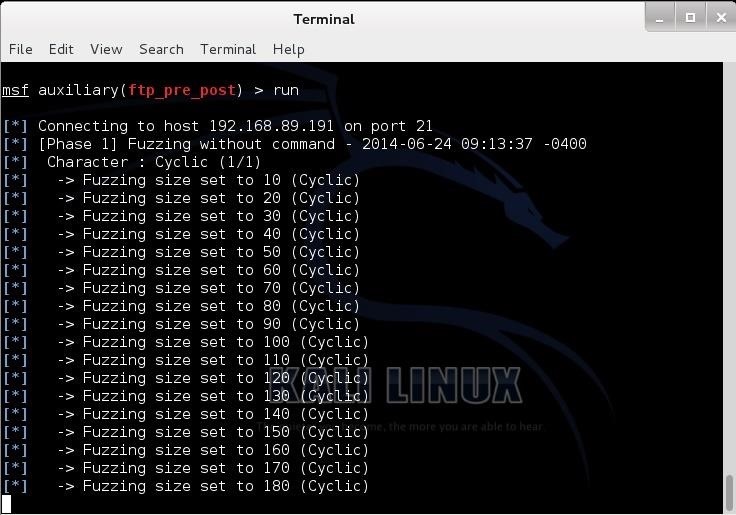
msf > run
As we can see above, the fuzzer begins by running random input set to size 10 bytes and increments the size by 10 each attempt. The default setting runs to size 20,000, but we can change that to any value that we find appropriate.
After attempting random input, it then begins to attempt various command inputs once again beginning at 10 bytes and incrementing by 10 to 20,000 bytes. It will stop when it finds two error messages or comes to the end of all of its attempts. Just a warning, this can take hours.
Keep coming back, my hacker novitiates, as we explore more Metasploit auxiliary modules and use them to find unknown vulnerabilities and progress toward developing our own zero-day exploits.
[the_ad id=”1250″]










I have been examinating out many of your posts and it’s clever stuff. I will surely bookmark your website.
Heya i am for the primary time here. I found this board and I in finding It truly helpful & it helped me out much. I’m hoping to offer one thing back and aid others like you helped me.
Like!! Thank you for publishing this awesome article.