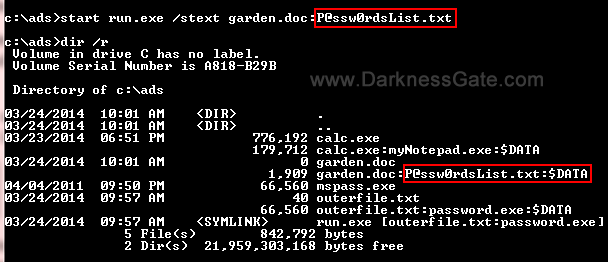
ANDROID MOBILE HACKS USING ANDROID DEBUG BRIDGE(ADB)
Hello friends, in this post, I will explain to you how you can exploit in Android device using open ADB port. Android Debug Bridge (ADB) is a command line tool that lets you communicate with an emulator or connected Android device. For this, we will use an open source script. PhoneSploit uses the Android Open…