Amap ( Application Mapping ) is designed to correlate applications that reside on a host to a specific port or port. Amap connects it to the port (s) and sends packets that will automatically respond in response. These packets typically involve a standard attempt by an application to perform a handshake between both hosts. Many network daemons respond only when a connection is attempted using an appropriate handshake (ie SSL). Amap ( Application Mapping ) then prints this response on its built-in library and screen.
Available from here
Execution:
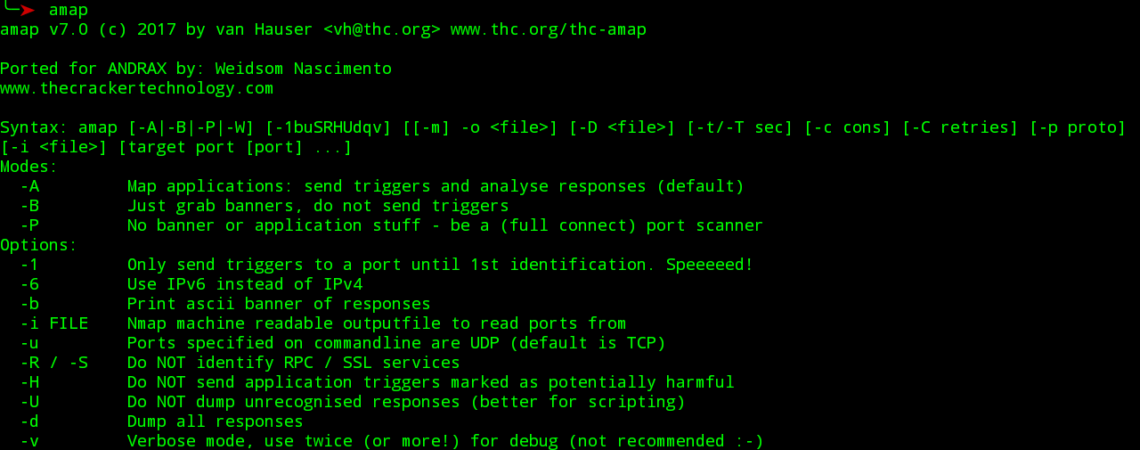
amap v5.3 (c) 2005 by van Hauser <amap-dev@thc.org> www.thc.org/thc-amap
Syntax: amap [-A|-B|-P|-W] [-1buSRHUdqv] [[-m] -o <file>] [-D <file>]
[-t/-T sec] [-c cons] [-C retries] [-p proto] [-i <file>]
[target port [port] …]
Modes:
-A Map applications: send triggers, analyse responses (default)
-B Just grab banners, do not send triggers
-P No banner or application stuff – be a port scanner
-W Web Update – online update the application fingerprint database!
Options:
-1 Only send triggers to a port until 1st identification. Speeeeed!
-6 Use IPv6 instead of IPv4
-b Print ascii banner of responses
-i FILE Nmap machine readable outputfile to read ports from
-u Ports specified on commandline are UDP (default is TCP)
-R / -S Do NOT identify RPC / SSL services
-H Do NOT send application triggers marked as potentially harmful
-U Do NOT dump unrecognised responses (better for scripting)
-d Dump all responses
-v Verbose mode, use twice+ for debug (not recommended 🙂
-q Doesn’t report closed ports, do not print them as unidentified
-o FILE [-m] Write output to file FILE,
-m creates machine readable output
-c CONS Amount of parallel connections default 32, max 256)
-C RETRIES Number of reconnects on connect timeouts default 3)
-T SEC Connect timeout in seconds (default 5)
-t SEC Response wait timeout in seconds (default 5)
-p PROTO Only send triggers for this protocol (e.g. ftp)
TARGET PORT The target address and port(s) to scan (additional to -i) amap is a tool to identify application protocols on target ports.
Usage hint: Options “-bqv” are recommended, add “-1” for fast/rush checks.










Like!! I blog quite often and I genuinely thank you for your information. The article has truly peaked my interest.